Apple has struck a big blow against the mercenary “surveillance-as-a-service” industry, introducing a new, highly secure Lockdown Mode to protect individuals at the greatest risk of targeted attacks. The company is also offering millions of dollars to support research to expose such threats.
Starting in iOS 16, iPadOS 16 and macOS Ventura, and available now in the latest developer-only betas, Lockdown Mode hardens security defenses and limits the functionalities sometimes abused by state-sponsored surveillance hackers. Apple describes this protection as “sharply reducing the attack surface that potentially could be exploited by highly targeted mercenary spyware.”
In recent years, a series of targeted spyware attacks against journalists, activists, and others have been exposed. Names including Pegasus, DevilsTongue, Predator, Hermit, and NSO Group have undermined trust in digital devices and exposed the risk of semi-private entities and the threat they show against civil society. Apple has made no secret that it is opposed to such practices, filing suit against the NSO Group in November and promising to oppose such practices where it can.
“Apple’s newly released Lockdown Mode will reduce the attack surface, increase costs for spyware firms, and thus make it much harder for repressive governments to hack high-risk users,” said John Scott-Railton, senior researcher at the Citizen Lab at the University of Toronto's Munk School of Global Affairs and Public Policy.
“We congratulate [Apple] for providing protection to human rights defenders, heads of state, lawyers, activists, journalists, and more,” tweeted the EFF, a privacy advocacy group.
What does Lockdown Mode do?
At present, Apple says Lockdown Mode provides the following protections:
- Messages: Most message attachment types other than images are blocked. Some features, like link previews, are disabled.
- Web browsing: Certain complex web technologies, like just-in-time (JIT) JavaScript compilation, are disabled unless the user excludes a trusted site from Lockdown Mode.
- Apple services: Incoming invitations and service requests, including FaceTime calls, are blocked if the user has not previously sent the initiator a call or request.
- Wired connections with a computer or accessory are blocked when an iPhone is locked.
- Configuration profiles cannot be installed and the device cannot enroll into mobile device management (MDM) while Lockdown Mode is turned on.
Ivan Krstić, Apple’s head of Security Engineering and Architecture, notes that Lockdown Mode can be applied to devices that are already enrolled in an MDM service. “Pre-existing MDM enrollment is preserved when you enable Lockdown Mode,” he tweeted.
The company says it intends to extend the protection provided by Lockdown Mode over time and has invested millions in security research to help identify weaknesses and increase the integrity of this protection.
How to enable Lockdown Mode
 Apple
Apple
Turning on Lockdown Mode. (Click image to enlarge it.)
- Lockdown Mode is enabled in Settings on iPhones and iPads and in System Settings on macOS.
- You’ll find it as an option in Privacy & Security, listed at the bottom of the page.
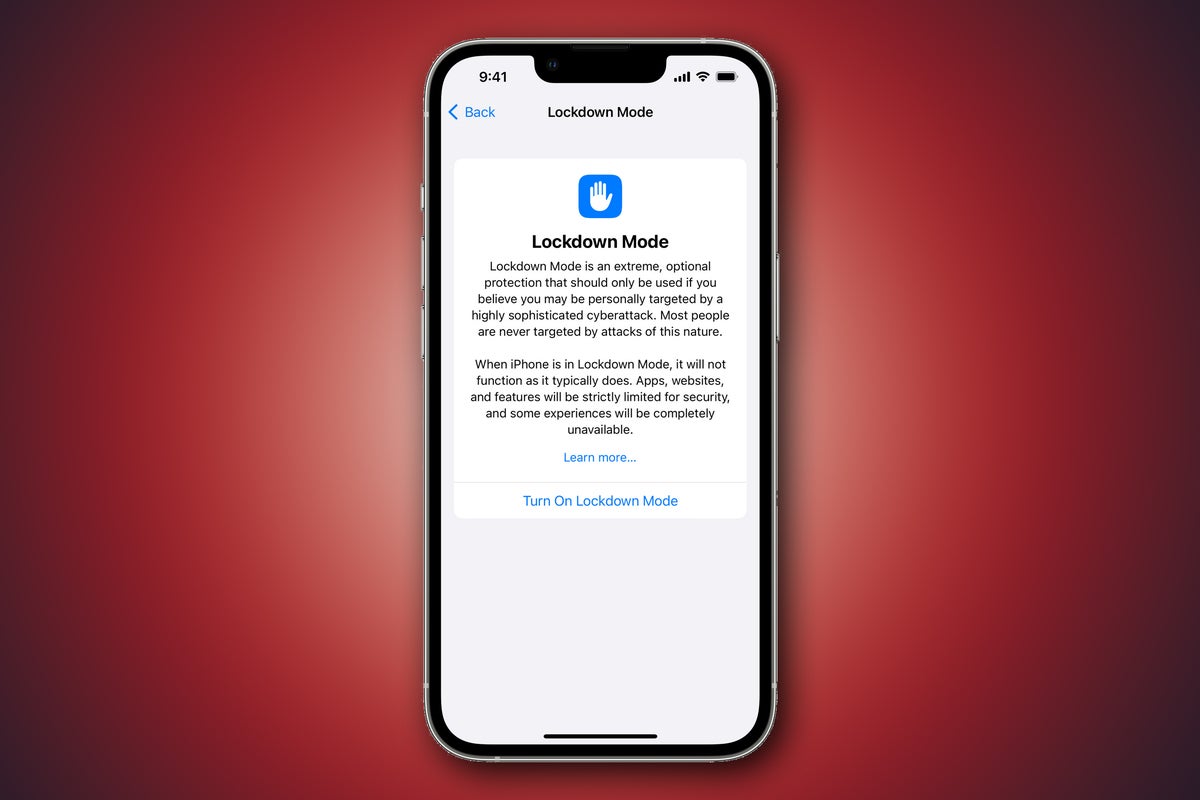
- Tap Lockdown Mode and you’ll be told that this provides “Extreme, optional protection that should only be used if you believe you may be personally targeted by a highly sophisticated cyberattack. Most people are never targeted by attacks of this kind.”
- The prompts also warn users that certain features will no longer work as you are used to. Shared albums will be removed from Photos, and invitations will also be blocked.
What is the scale of this threat?
These attacks don’t come cheap, which means most people are unlikely to be targeted in this way. Apple began sending threat notifications to potential victims of Pegasus soon after it was revealed and says the number of people targeted in such campaigns is relatively small.
All the same, the scale is international, and the company has warned people in around 150 nations since November 2021. A BBC report confirms hundreds of targets and tens of thousands of phone numbers leaked as a result of NSO’s Pegasus alone. Victims have included journalists, politicians, civil society advocates, activists, and diplomats, so while the numbers are small, the chilling impact of such surveillance is vast.
I believe that such technologies will become cheaper and more available over time, so it’s only a matter of time before they leak into wider use. Ultimately the very existence of such attacks — state-sponsored or not — makes the entire world less safe, not safer.
“There is now undeniable evidence from the research of the Citizen Lab and other organizations that the mercenary surveillance industry is facilitating the spread of authoritarian practices and massive human rights abuses worldwide,” said Citizen Lab Director Ron Deibert in a statement. Deibert told CNET he thinks Lockdown Mode will deal a "major blow" to spyware companies and the governments that use their products.
“While the vast majority of users will never be the victims of highly targeted cyberattacks, we will work tirelessly to protect the small number of users who are,” said Apple's Krstić in a statement. “That includes continuing to design defenses specifically for these users, as well as supporting researchers and organizations around the world doing critically important work in exposing mercenary companies that create these digital attacks.”
There’s little doubt Microsoft and Google will also move to provide similar protection to users. Google and Meta already offer tools to secure the accounts of those who are at an “elevated risk of targeted online attacks,” but these tools don’t go nearly as far as Lockdown Mode.
Apple’s investments in security
Apple already makes vast investments in security. For example, the company is working with others in the industry to support password-free authentication, has built tools to mask IP addresses and continues to focus on user privacy.
The company will introduce a Rapid Security Response feature for its devices this fall, which will make it possible to deploy security fixes outside of full security updates and much more. Apple is even investing in improving the security of programming languages, further eroding potential attack surfaces.
The company has now announced further investment in the security community:
- Apple has also established a new category within the Apple Security Bounty program to reward researchers who find Lockdown Mode bypasses and help improve its protections. Bounties are doubled for qualifying findings in Lockdown Mode, up to a maximum of $2,000,000 — the highest maximum bounty payout in the industry.
- Apple is also making a $10 million grant, plus any damages awarded from the lawsuit it is pursuing against NSO Group, to support organizations that investigate, expose, and prevent highly targeted cyberattacks, including those created by private companies developing state-sponsored mercenary spyware. It is giving this money to the Ford Foundation’s Dignity and Justice Fund.
What will the Dignity and Justice Fund do?
The fund will make its first grants later this year, focusing initially on initiatives to expose the use of mercenary spyware. In the press release announcing the initiative, Apple tells us these grants will focus on:
- Building organizational capacity and increasing field coordination of new and existing civil society cybersecurity research and advocacy groups.
- Supporting the development of standardized forensic methods to detect and confirm spyware infiltration that meet evidentiary standards.
- Enabling civil society to more effectively partner with device manufacturers, software developers, commercial security firms, and other relevant companies to identify and address vulnerabilities.
- Increasing awareness among investors, journalists, and policymakers about the global mercenary spyware industry.
- Building the capacity of human rights defenders to identify and respond to spyware attacks, including security audits for organizations that face heightened threats to their network
The fund’s grant-making strategy will be advised by a global Technical Advisory Committee. Initial members include Daniel Bedoya Arroyo, digital security service platform analyst at Access Now; Citizen Lab Director Ron Deibert; Paola Mosso, co-deputy director of The Engine Room; Rasha Abdul Rahim, director of Amnesty Tech at Amnesty International; and Apple's Krstić.
Ford Foundation Tech and Society Program director Lori McGlinchey said:
“The global spyware trade targets human rights defenders, journalists, and dissidents; it facilitates violence, reinforces authoritarianism, and supports political repression. The Ford Foundation is proud to support this extraordinary initiative to bolster civil society research and advocacy to resist mercenary spyware. We must build on Apple’s commitment, and we invite companies and donors to join the Dignity and Justice Fund and bring additional resources to this collective fight.”
What else can you do?
Following revelations about NSO Group last year, Apple published a set of recommendations to help users mitigate against such risks. These guidelines do not even approach the kind of robust protection you can expect from Lockdown Mode, but it makes sense for anyone to follow such practices:
- Update devices to the latest software, which includes the latest security fixes.
- Protect devices with a passcode.
- Use two-factor authentication and a strong password for Apple ID.
- Install apps from the App Store.
- Use strong and unique passwords online.
- Don’t click on links or attachments from unknown senders.
Furthermore, Amnesty Tech is gathering signatures to demand an end this kind of targeted surveillance of human rights defenders. I’d urge readers to add their signature to my own.
Please follow me on Twitter, or join me in the AppleHolic’s bar & grill and Apple Discussions groups on MeWe.