When Apple CEO Tim Cook in 2016 warned of a cybersecurity war, he was specifically discussing the pressure Apple then faced to create back doors on its platforms so law enforcement could snoop on users.
He was championing encryption and opposing the creation of designer vulnerabilities that can be exploited by any entity that knows they exist. Since then, we’ve seen a cancerous tumult of surveillance as a service that companies such as the NSO Group break out, each of them using the kind of hard-to-find flaws governments may insist on platform providers creating.
These back doors make no one safe.
Worse still, we’ve also seen that they do eventually leak beyond the relative constraints of eye-wateringly expensive private digital spook services. Take the recent appearance of Atomic macOS Stealer, a fee-based Mac attack "service" that can be used to exfiltrate critical data, including passwords, documents, images and more. It’s available to anyone with a few dollars to spare.
This is not good. It is nowhere near good.
Digital security is a battleground
With nation states at loggerheads, it’s sadly predictable that heaps of cash will be thrown at cracking security on any platform, not just Apple’s — and to protect against this most vendors are working towards systems that work like Apple’s Rapid Security Response.
That solution has been developed so that Apple can swiftly distribute critical software updates across its entire ecosystem of devices. The idea is that the company can patch critical vulnerabilities as swiftly as possible once they've been identified and a patch made.
As Cook observed, such rapid security remediations are mandatory in an increasingly complex threat environment. Speaking to Time all those years ago, he was already aware of the threat and the extent to which it has changed.
“With hacking getting more and more sophisticated, the hacking community has gone from the hobbyist in the basement to huge, sophisticated companies that are essentially doing this, or groups of people or foreign agents inside and outside the United States. People are running huge enterprises off of hacking and stealing data. So yes, every software release we do, we get more and more secure,” he said.
He added, “You can’t have a back door that says good people only. It doesn’t work that way.”
Apple’s focus on security
A lot has happened in the last seven years. The company’s security teams have raised their game with a flotilla of protective charms to secure the company’s platforms. These span everything from Declarative Device Management to Lockdown Mode, and encompass APIs such as the Endpoint Security Framework already in use by MDM vendors to give devices more real-time situational awareness of attacks.
Of course, awareness is one thing. But no force in the field can do much with that information unless it can respond flexibly and fast to any identified attack. The prevalence of nation- and near-nation-state attacks that exploit zero-day flaws requires platform vendors be ready to respond swiftly.
This is what Apple’s now-emerging Rapid Security Response system is for.
Rapid Security Response — the new front line
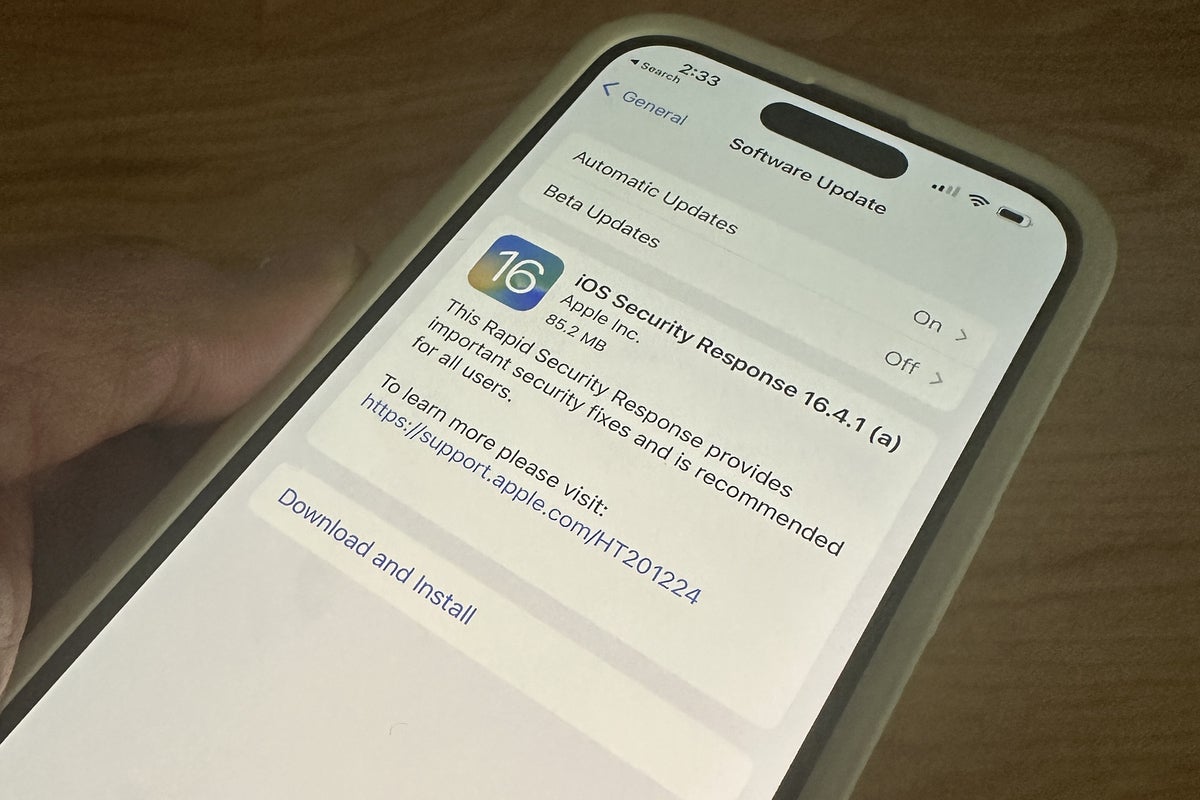
Rapid Security Response updates are applied automatically by default. You can ensure the protection is enabled in the Security Responses & System Files setting inside Software Updates>Automatic Updates on iPhones, iPads, or in Automatic Updates inside Software Updates on the Mac. In the future, your system should download and install these updates when they appear.
This is war, and make no bones about it, Rapid Security Response is an important part of Apple’s security front line. It’s the tactical fast response point at which emerging threats will be opposed by increasingly agile security response teams. As new vulnerabilities are identified, security patches will be rolled out swiftly to plug them up.
The process is clearly more complex than it sounds. The protection was announced last summer, but only saw real action this week and there were unknown initial distribution problems, which appear to have been resolved.
Security is a constant ebb and flow.
The war continues, prepare for a quantum leap
Digital terrorists will keep trying to overcome Apple’s protections as fast as it puts them in place. With this in mind, old notions of platform-based security superiority need to be abandoned in favor of a more cynical and inherently more depressing outlook of threat awareness. In this picture, every organization must build in additional redundancies, prepare backup and remediation plans, and deeply consider every public facing element of their stack, from access, to cloud, to email, to zero trust and beyond.
It’s not enough to prepare against potential threats; experts warn business must get ready for inevitable attacks. Not only this, but the coming quantum computing-driven security test will require incredibly fast platform based remediation and response to emerging threats. That's why Rapid Security Response has become the new front.
Are your systems on the right side of the line? And how will Apple extend these protections at WWDC?
Please follow me on Mastodon, or join me in the AppleHolic’s bar & grill and Apple Discussions groups on MeWe.